Fix invalid id token issue in WSO2 Identity Server 5.11.0
You might come across id token validation issues in the Wso2 Identity Server 5.11.0. This article discusses possible fixes. …
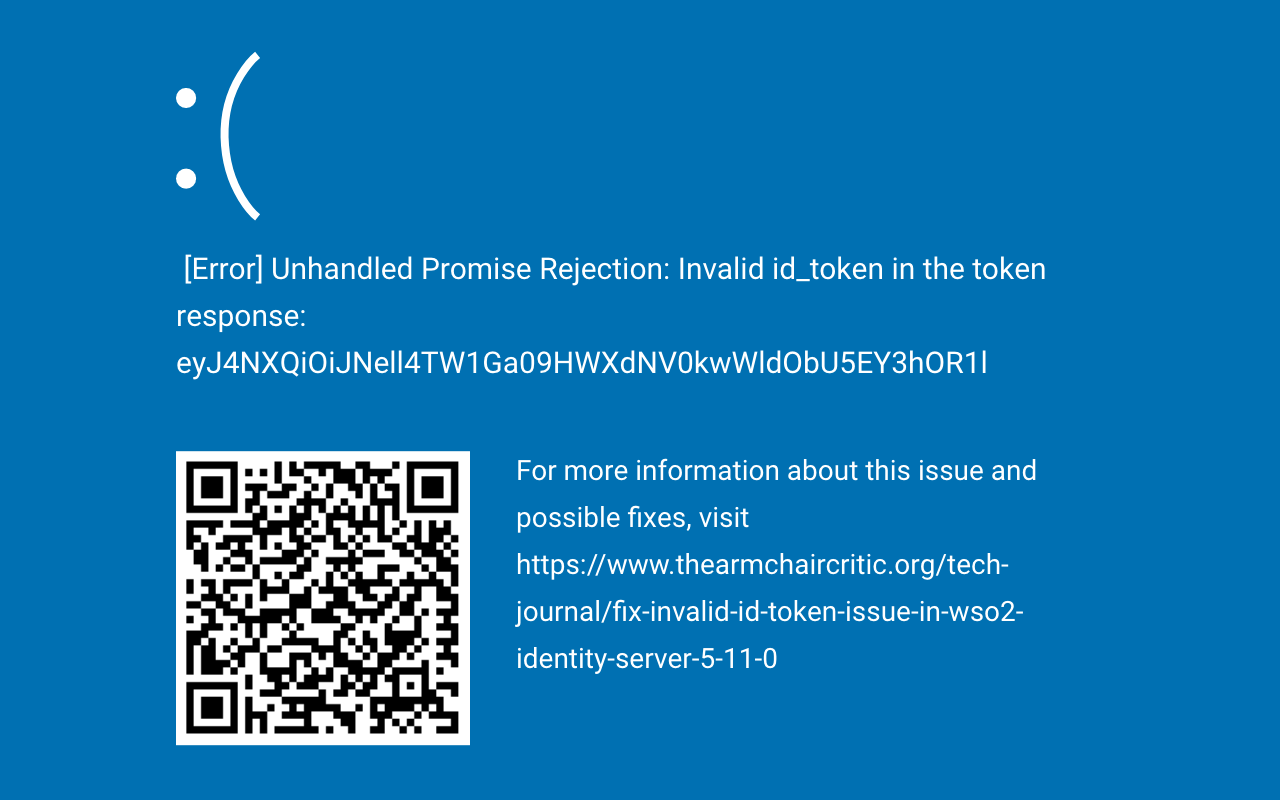
You might come across id token validation issues in the Wso2 Identity Server 5.11.0. This article discusses possible fixes. …

The R language allows for rapid prototyping of machine learning and neural network models. Having learned to create neural networks using Python, I found prototyping neural networks using R to be quick and easy. Even…
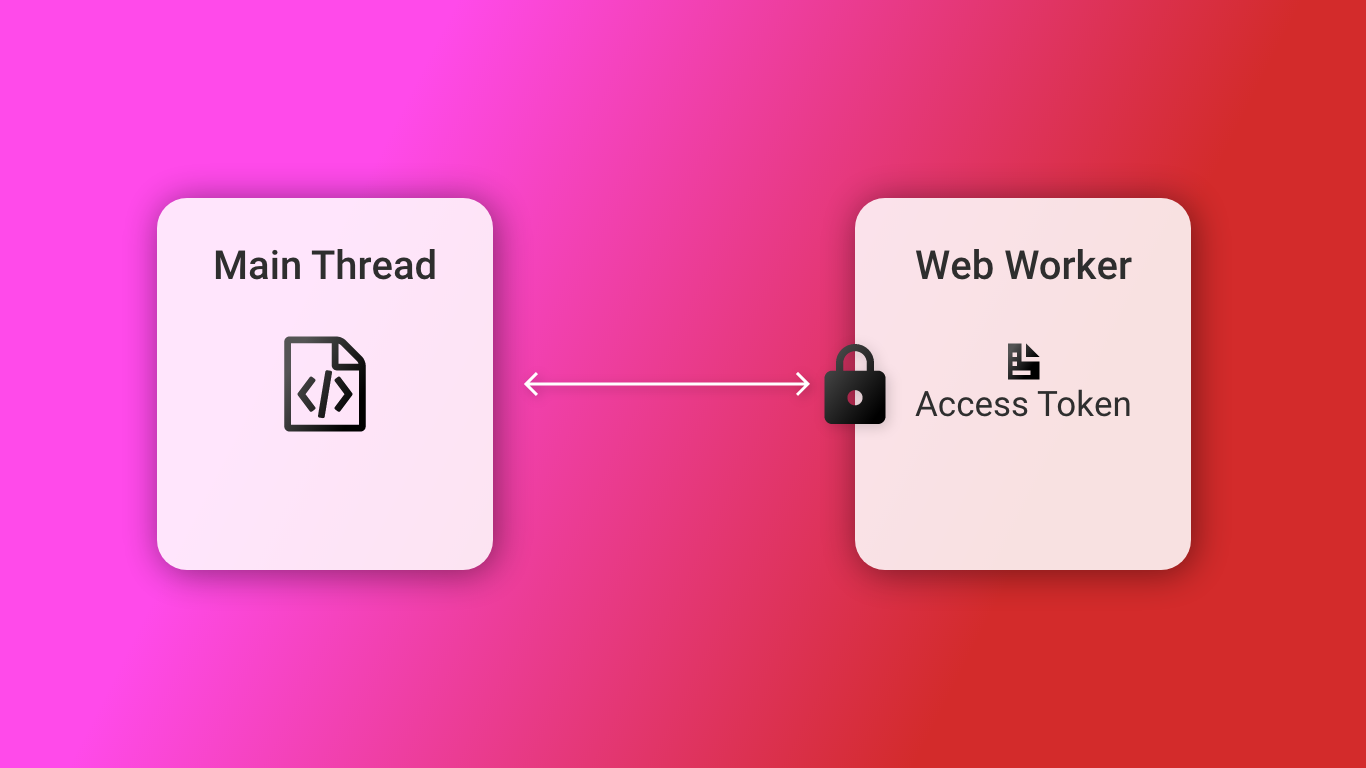
We use web workers to offload resource-intensive tasks to a background thread in a web app. But did you know we can also use them to safely store access tokens? This article discusses how it…

If you have used the OIDC protocol to implement single sign-on, you would be used to receiving the authorization code as a query parameter from the identity server. However, did you know that receiving the…

WSO2 Identity Server allows you to integrate Azure Active Directory as a federated identity provider out of the box using the OIDC protocol. However, there may be times you may want to integrate Azure Active…
WSO2 Identity Server has always been known for its technical brilliance and feature richness. But that wasn’t enough to satiate us. In order to provide an unparalleled user experience, we wanted to add one more…
Asgardio OIDC JavaScript SDK allows developers to implement OIDC authentication in their Single Page Applications in a fast and secure manner, especially when using the WSO2 Identity Server as the Identity Provider. The SDK offers three…
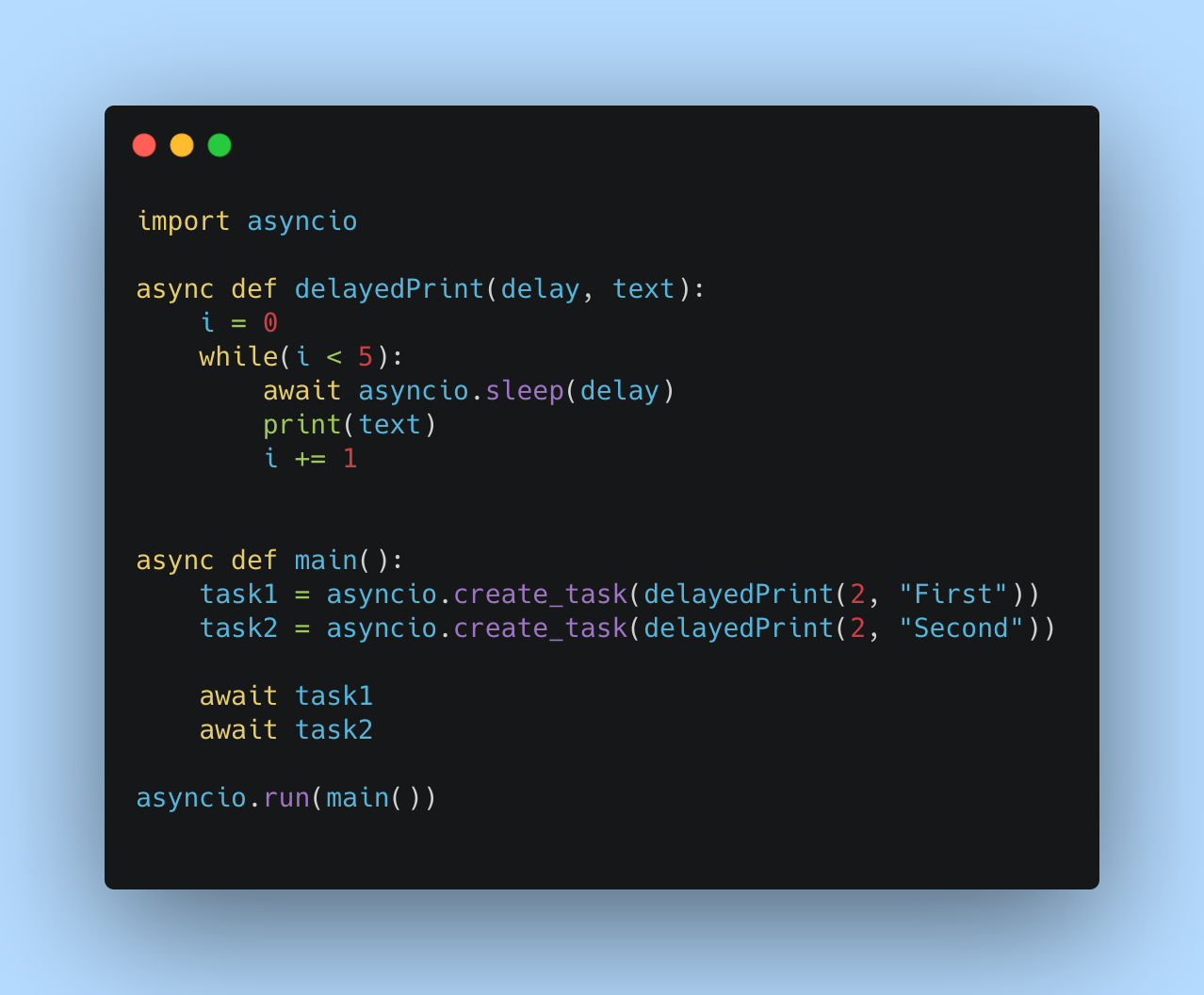
Python’s Async IO has made writing concurrent applications a breeze. This article explores how Async IO can be used to achieve concurrency in Python.…

The C in CIAM stands for the customer; this means that a business that wants to attract and retain customers should ensure that customer needs are met first. This post discusses some common mistakes we,…

GitHub Actions has made CICD easy. Couple it with the free hosting service offered by Firebase, you have a fully functional CICD pipeline ready for your frontend app completely free in no time. As frontend…
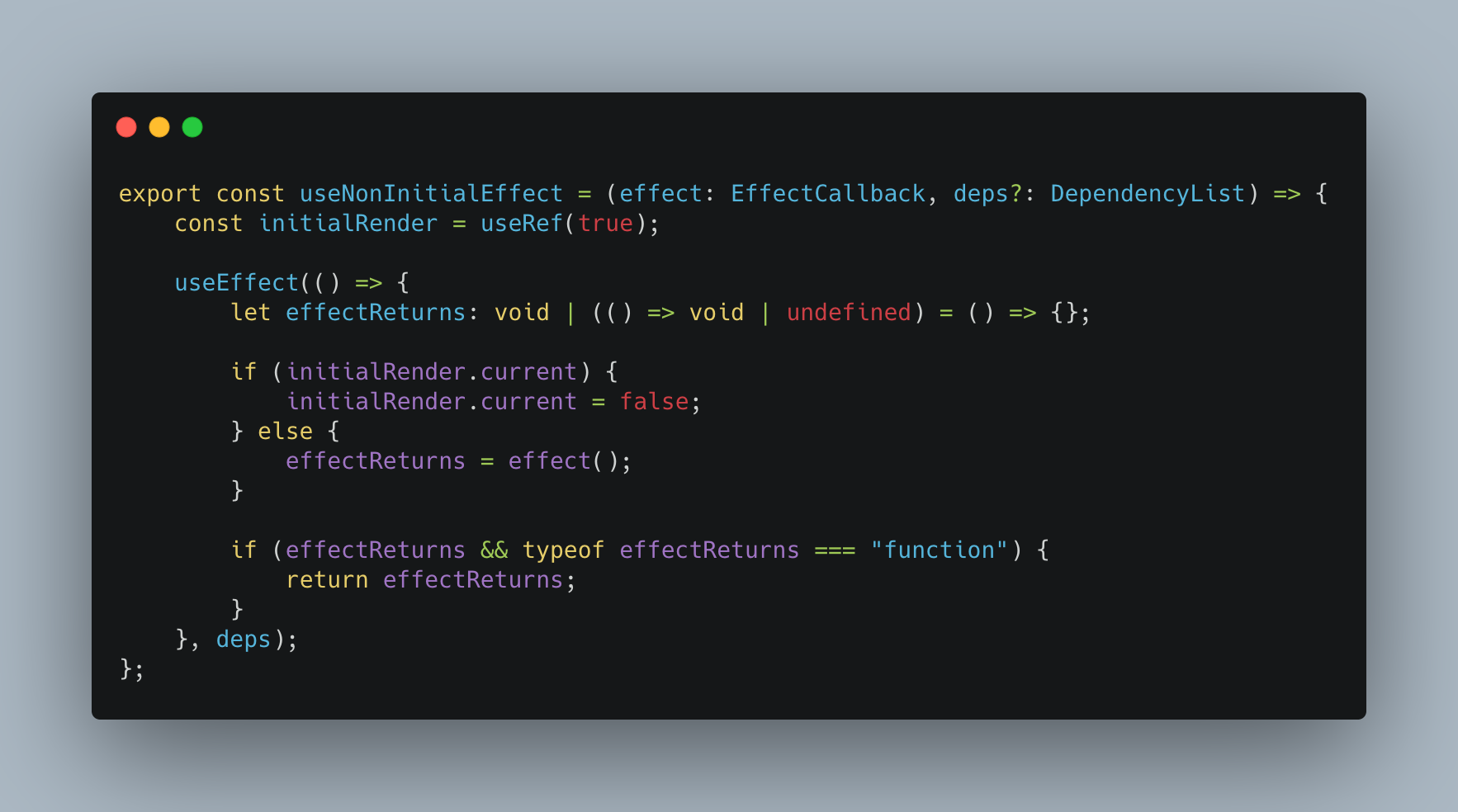
React’s useEffect hook has indeed made life a lot easier. But there are times when you would most certainly miss the fine-grained control class-based components give you over a component’s lifecycle. One such time is when you…
Unless you have been living under a rock, you would be very used to authenticating yourself using an authenticator app on your mobile phone. But have you ever wondered how an online service is able…
Before smartphones were popular, hardware tokens that produced an HOTP code were a popular way of performing two-factor authentications. Businesses gave their customers a small electronic device that generated a number when a button was…

HMAC stands for Hash-based Message Authentication Code or Keyed-hash Message Authentication Code. We use it to verify the authenticity and integrity of data transmitted. Here, authenticity is ensuring that the data was indeed sent by…
I recently had to install and configure Jest in a React app written using Typescript and ran into quite a few roadblocks. So, I thought of detailing the steps I followed to overcome the difficulties.…

Lerna comes to our rescue when we are to manage multiple inter-dependent packages within a repository. Have a package that is a dependency of another and you don’t want to waste time building the dependency,…